The EU Cyber Resilience Act (CRA) redefines product security. So, what do OT products need to do to stay in the game in the EU? Let’s dive in!
Product and manufacturer requirements
The CRA targets all “products with digital elements” that can communicate, covering both hardware and software. It sets mandatory guidelines that must be followed when placing products on the market. Compliant products get the CE mark, while non-compliant ones will not be allowed. This applies to existing products too. Manufacturers, distributors, and importers are all on the hook for ensuring compliance.
Process Requirements
Secure development is just the start. Vulnerabilities must be fixed “promptly,” with security updates provided for free over five years. Products also need to be actively monitored for vulnerabilities during this period.
Manufacturers must report actively exploited vulnerabilities and security-relevant attacks to ENISA within 24 hours.
Spotlight on CRA conformity assessment
Before hitting the market, products must be assessed for compliance. Depending on the product’s criticality classification under the law, appropriate standards must be considered.
The CRA is designed as a dynamic system, allowing the Commission to update the list of important products defined in Annex III through a legal act. This means that these products must be assessed using stricter conformity assessment procedures.
A Class I product performs essential functions important for the cybersecurity of other products, networks, or services and poses a significant risk of direct manipulation of a large number of other products.
Important Class I products include: routers, modems, switches, VPN devices, public key infrastructures and their software, SIEM systems, and microprocessors with security-relevant functions.
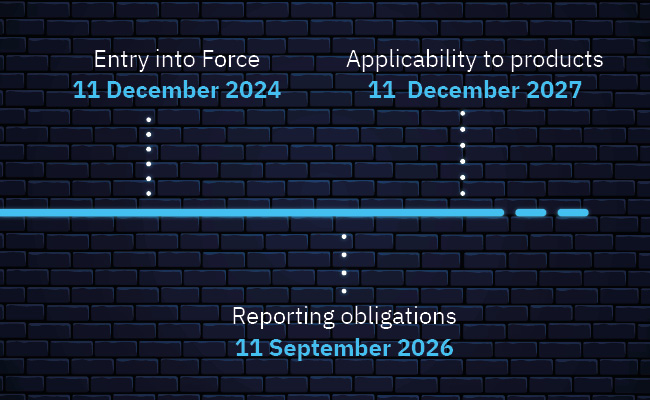
The road ahead: Key dates to remember
The CRA was officially published on November 20, 2024. By September 11, 2026, all products must have a compliant vulnerability management system. Full CRA implementation is required by December 11, 2027. By then, all relevant products must meet the requirements to get the CE mark.
Requirements for products with digital elements
Annex I of the CRA outlines basic product requirements, focusing on secure design, development, and manufacturing. Key areas include access protection, confidentiality, integrity, availability, and secure delivery.
Annex I emphasizes risk assessment for intended use. Full implementation of requirements depends on the product’s risk analysis and security context. In OT, this means deployment scenarios in the production network.
Here are some of the 13 key requirements:
- Free from known exploitable vulnerabilities.
- Delivered with a secure default configuration.
- Capable of addressing security vulnerabilities through updates.
- Equipped with authentication, identity, or access management systems that report unauthorized access.
- Protect data integrity and report any damage.
- Ensure availability of essential functions even after security incidents like denial-of-service attacks.
- Minimize the impact of security incidents on other devices or network services.
OT relevant additions
The final text includes three OT-specific clarifications:
- Spare parts can be replaced in machines even if they don’t comply with the CRA.
- Composite products can be classified by their core functions, even if sub-functions require stricter assessments.
- Recognized interoperability standards can be used, even if their security features are outdated. This could ease the use of industrial communication, though this is only mentioned in the recitals, not the legal text.
IEC 62443-4-1 / 4-2: The gold standard for CRA compliance
Guidelines for conformity proof are being defined for specific product classes, largely based on IEC 62443. This global standard for cybersecurity in automation is crucial for certain applications and demonstrating cybersecurity in companies and products.
Applying and certifying according to IEC 62443 is a solid foundation for CRA compliance, especially for products that can use self-assessment.
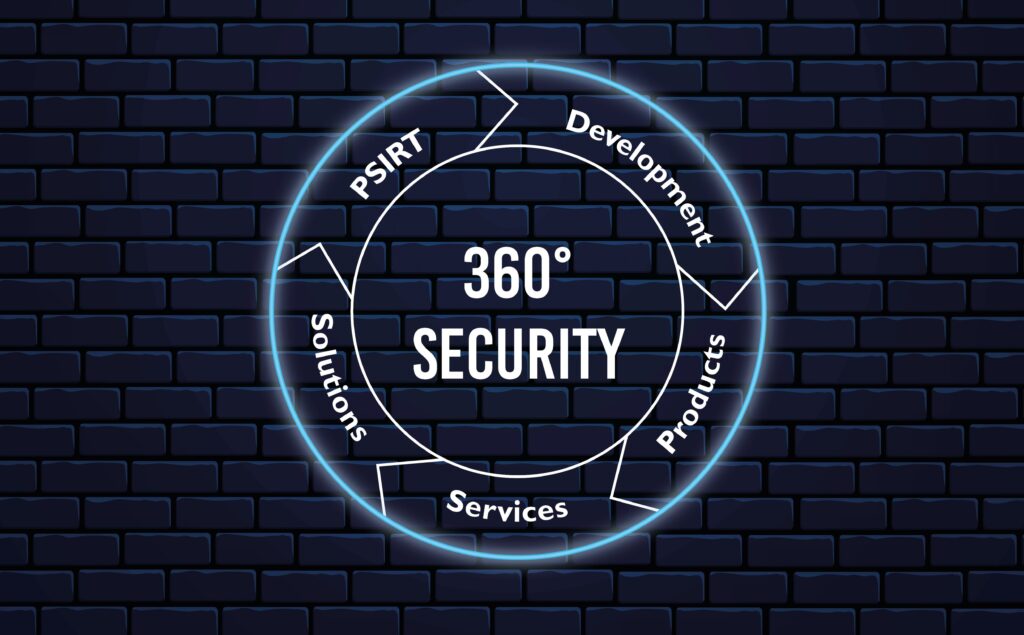
Our 360° Security Concept
Phoenix Contact started implementing IEC 62443 in 2017, establishing the “360° Security Concept.” Secure products like our PLCnext Control AXC F 2152 are developed according to IEC 62443-4-1 and meet the security function requirements of IEC 62443-4-2. Vulnerability management is handled by the Product Security Incident Response Team (PSIRT). Secure solutions and services are also offered.
The cybersecurity processes are independently certified by TÜV Süd and reviewed annually.
Conclusion
The Cyber Resilience Act will significantly boost cybersecurity in OT. However, products must also be securely configured and operated. An information security management system (ISMS) is still essential, considering the necessary organizational measures. The EU’s Network and Information System Directive (NIS 2) defines cybersecurity for operators.
Read this article for more information on the new EU directive NIS 2.
In case you want to read more about industrial cyber security we welcome you to Phoenix Contact´s main page about industrial security. Discover the full potenial of a 360-degree security contect and get inspired by the holistic product and service portfolio of Phoenix Contacts Industrial Security.
If you want to get more information about PLCnext Technology and Cybersecurity, you are welcome to read our article Next Level of Security at our PLCnext Community Website.