
Safety plays a central role in automation. In the past, the areas of safety and security could be considered separately. However, digitalization and the networked automation systems of Industry 4.0 are creating mutual dependencies that require a holistic concept. In the following article, you will learn more about what happens when safety meets security and what you should consider for a holistic concept.
The area of safety (functional safety) deals with the protection of people from machines. The goal is freedom from intolerable risk. In a risk analysis, the danger posed by a machine to people is evaluated. The risks are minimized by organizational, constructive, and technical measures. In a sense, this is a “battle against natural laws”.
Security, on the other hand, is concerned with protecting the machine from the human being. The goal is freedom from intolerable risk. In a risk analysis, the danger posed by people to a machine is assessed. The risks are minimized by organizational, constructive, and technical measures. In a sense, this is a “battle against brains”.
While functional safety is still mainly considered locally today, external influences have always had to be considered in security. With increasing networking, functional safety functions and components are also accessible via network communication, so that local consideration of safety components will soon no longer be sufficient to prevent new opportunities for attack.

Functional safety
The implementation of the requirements from the Machinery Directive (MRL) is a binding requirement through the Product Safety Act. The MRL specifies a uniform level of protection for the manufacture of machinery with safety and protection requirements for accident prevention. It applies to products sold throughout the European Economic Area (EEA) and is specified in more than 700 harmonized standards.
Among other things, the MRL requires that a risk assessment be carried out for each machine at the time of construction. For each phase of life, the possible hazards that may occur must be determined and assessed. Each hazard is considered individually regarding the severity of the hazard, probability of occurrence and possibility of avoidance. This results in the respective risk factor. If this is higher than permitted, then the manufacturer must take risk-reducing measures: First constructive (e.g. an adjustment of the geometric design of parts) , then technical (e.g. separating protective devices) and finally indicative measures (e.g. warning or safety instructions in the accompanying technical documentation such as the operating instructions). If technical measures are implemented to reduce risk, these are referred to as functional safety measures.
Harmonized standards such as EN ISO 13849-1, EN 62061 or EN 61511 contain requirements for achieving functional safety. The reliability of the safety functions can be assessed based on the achieved safety level or safety integrity level (SIL for short). This results in the safety-oriented design principles that must be fulfilled to minimize the risk posed by the machine. The standards use different terms here: While EN ISO 13849-1 speaks of a performance level, EN 62061 speaks of a SIL.
Special standards and guidelines apply to safe components and safe controls, which are generally subject to even stricter requirements.

Security
In the area of security, there have been far fewer legal requirements to date, as security tends to pursue economic goals rather than the protection of people and the environment in general.
(There are exceptions, however, for example in the process industry when hazardous substances are processed. Here, incidents can be correspondingly sensitive. Operators of corresponding operating areas must take the Hazardous Incident Ordinance into account.)
The security objectives are confidentiality, integrity and availability of the data and the service.
The IT Security Act applies to companies from the telecommunications industry, providers of digital services and operators of critical infrastructures (CRITIS). This is a legal framework for cooperation between the state and companies with the aim of greater cyber security. It states, for example, that KRITIS operators must implement IT security in accordance with the “state of the art” and report significant IT security incidents to the BSI (German Federal Office for Information Security) and the respective customer.
The European Network and Information Security Directive (NIS Directive) defines measures to ensure a high common level of security of network and information systems in the Union. The NIS Directive was transposed into national law by the EU member states and essentially serves to implement the NIS Directive. The publications of the BSI[1] provide a good overview on the topic of security in automation.
IEC 62443 is a series of standards for cybersecurity in automation.
Risk and threat analysis is also carried out in the area of security. However, the threats posed by people and organizations are more difficult to assess quantitatively than threats posed by machines. Standards classify attacker motivation and capabilities into classes, which are used to determine a corresponding need for protection. This assessment is less precise than a risk and threat analysis in the area of safety and leaves some room for interpretation.
The protection goals of Security and Safety can collide when it comes to how a safe state can be achieved in the event of a fault. An example: In the event of a fault, the operation of a system is shut down in order to maintain the protection goals of confidentiality and integrity. This collides with the protection goal of availability, an important protection goal in automation. Priorities must be set here: The protection of people outweighs the availability of the plant.
Another challenge is dealing with vulnerabilities: Attackers are constantly finding new methods to uncover vulnerabilities in implementations or protocols and use them for their criminal purposes. For this reason, it is necessary in security to constantly reassess the threat situation (keyword “moving target”).
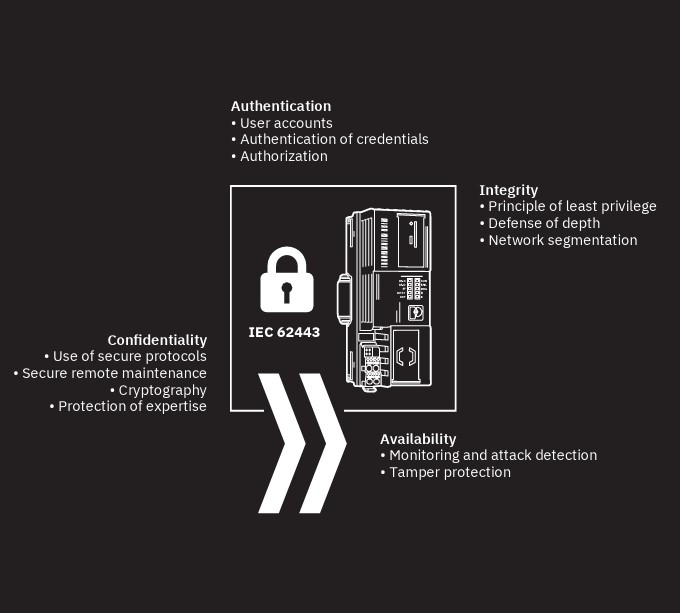
Interactions between safety and security
The exact interaction of safety and security must be analyzed separately in each automation project, also regarding the possible measures for danger prevention. After all, a system that is 100% safe in terms of security is hardly practical to implement and use, let alone cost-efficient. But: Security poses a potential threat that brings with it new risks for people in terms of functional safety. The keyword here is tamper resistance in functional safety. The important question here is: What impact do these new risks have on the established standards of functional safety and how can the new risks be minimized to a tolerable residual risk through suitable organizational or technical measures?
The protection goals of Safety and Security should be combined so that the protection goals of Security support the protection goals of Safety:
- Security protection goal Integrity for functional safety:
Detect and/or prevent manipulation of safety-relevant functions and, if necessary, transfer them to the safe state. - Security protection goal Availability for functional safety:
Make security-relevant functions usable as scheduled. - Security protection goal Confidentiality for functional safety:
Protect information (security-relevant and non-security-relevant) whose theft and misuse could compromise functional safety.
A holistic concept
In the case of cross-company networking, the following points are important in terms of functional safety and security:
- Common security levels across all partners sharing data and information.
- Models for cross-enterprise, secure identification and definition of roles of all participants as well as coordinated access procedures and rights.
- Create legal frameworks to regulate data sharing (e.g., ownership of data).
- When machines are converted, modified or adapted at short notice for production purposes, functional safety must be ensured. For this purpose, systems and models must be defined and described that support this, among other things, with regard to the verification of functional safety.
- There are no universal solutions for all applications: Each system must be analyzed individually and a holistic concept adapted to the individual case must then be created. Safety and security experts must work together to achieve this.
- The company’s own personnel must be informed, instructed and continuously trained.
- A continuous build-up of know-how that is adapted to the constantly changing requirements and threats of security.
Phoenix Contact’s product and solution portfolio includes many specific products on the topics of functional safety and security. In the area of functional safety, the portfolio ranges from safety relays and configurable safety solutions to central safety controllers. In the area of security, the mGuard product family provides state-of-the-art solutions for network security and secure remote maintenance. Phoenix Contact supports its customers in their projects with specific consulting. The range of services in the area of functional safety has been tried and tested for many years. In the area of IT security, the available range is being further expanded. Phoenix Contact can thus provide support in the holistic approach.
In the sense of a security-by-design approach, security must be considered from the very beginning of product development. This approach has been consistently implemented in the products of PLCnext Technology.
And: At Phoenix Contact, clever minds are working at full speed to further combine the requirements of functional safety with the security requirements of modern safety controllers. PLCnext Technology will be the key here as well: The AXC F XT SPLC 1000 is a safety-oriented controller.
It is operated as a left-side expansion module on an AXC F 2152 or AXC F 3152. This creates a fully-fledged safety-oriented system that meets requirement level SIL 3. The SPLC 1000 can communicate with PROFIsafe devices via Axioline F local bus and Ethernet. You will find out more at the latest at the SPS in November. Stay tuned!
[1] Only available in German language, accessed 13.02.2021




