TÜV certified protection against cyber-attacks according to IEC 62443-4-1 ML3 and IEC 62443-4-2 SL2
Secure is secure! Especially when it comes to industrial cyber security. Because cyber-attacks on industrial companies are increasing exponentially. Not only in the German market, but also internationally, cyber-attacks are on the rise. This form of crime occurs in various forms: Industrial espionage, data theft, but also extortion of sums of money through paralyzed productions are possible.
Under the keywords IIoT and Industry 4.0, digitally networked systems and processes are standard. They offer a lot of potential for possible cyber-attacks due to closely linked interfaces. Therefore, any participant in an automation solution that is already inherently protected against cyber-attacks makes it easier to secure the overall system. With the progressive merging of IT and OT during IoT solutions, protection against hacker attacks is no longer limited to classic IT.
For this reason, some of our PLCnext Technology products are certified by TüV Süd with IEC 62443-4-1 and 62443-4-2. according to industrial cyber security. This means that both the ´secure product development lifecycle´ as well as the ´technical security requirements´ for industrial IT security are certified by TüV Süd. Our PLCnext Control are the first PLCs on the market in the automation industry with an IEC 62443-4-2 SL2-certified scope of functions!
Following PLCnext Technology products are certified according to IEC 62443-4-1 and 62443-4-2:
- PLCnext Control: AXC F 1152, 2152 and 3152
- PLC extension modul: AXC F XT SPLC 1000
- Safety Controller: RFC 4072S and BPC 9102S
What the certification means exactly, and which concrete advantages result from it for the user, we would like to bring you closer in the following article. Enjoy reading.
Let´s start with some basics
These are figures that make people sit up and take notice: The monetary damage caused by cyberattacks on IT has increased almost tenfold in the last ten years. This is confirmed by analyses of the Internet Crime Complaint Center for IT institutions in the USA. The “IC3” works under the umbrella of the FBI and has calculated damages of 4.2 billion dollars for 2020. Ten years earlier, the agency reported 485 million dollars – and these are only the proven damages, i.e. figures from forensic criminal prosecution.
In industrial production, it is primarily factory equipment that needs to be securely protected against attacks. This requirement is comparatively new. Ten years ago, protection against hackers was more the domain of classic “office” IT. “Automation controllers often hung open on the network. Anyone who knew the network address – i.e., the IP – had easy manipulation options,” Boris Waldeck, security expert at Phoenix Contact, looks back. “There are IP search engines that allow me to search the Internet for openly accessible controllers.”
Balancing act between security and networking
The fact that seemingly little happened in the past can be explained primarily by the fact that the data infrastructure in the production environment was not in focus from the hackers’ point of view. This was because the automation data systems were clearly separated from the IT networks. However, this separation is dissolving more and more in the course of digitalization and the associated dissolution of the boundaries between IT and OT. IoT and Industry 4.0 create new motivations and intrusion paths for criminal activities. Therefore, it is more important than ever to make the store floor secure. Security is thus becoming a new discipline in the development of individual machines and the construction of entire plants. Just how important the whole thing has become in the meantime is demonstrated, among other things, by the fact that there is a separate global standard for cyber security in the form of IEC 62443 for “Operation Technology” (OT). The whole thing goes as far as certification – in Germany, for example, by TÜV Süd.
Security starts with every single control
In view of the growing threat scenarios in industry, it is extremely effective to use control technology that is already inherently safe. For the user, this means that fewer security components need to be integrated into the automation system. This not only makes the overall system leaner, but also saves costs and time.
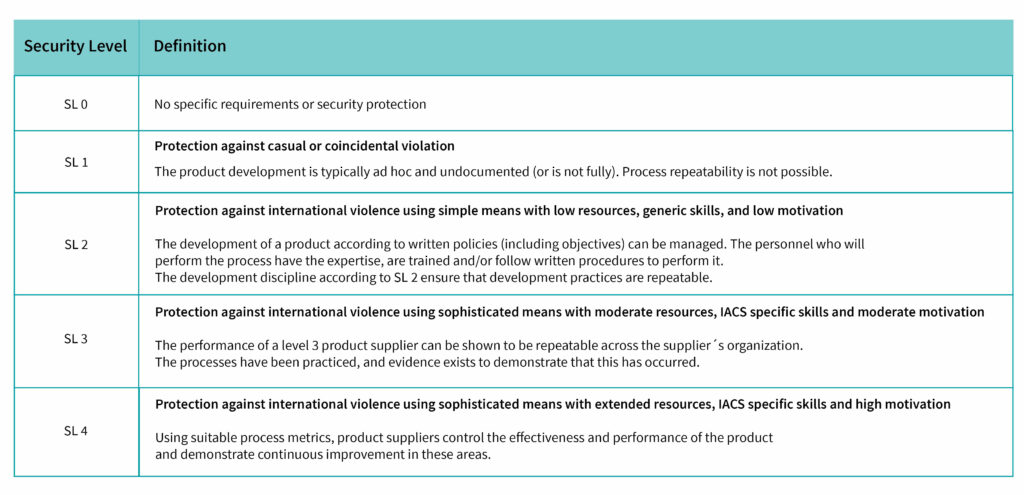
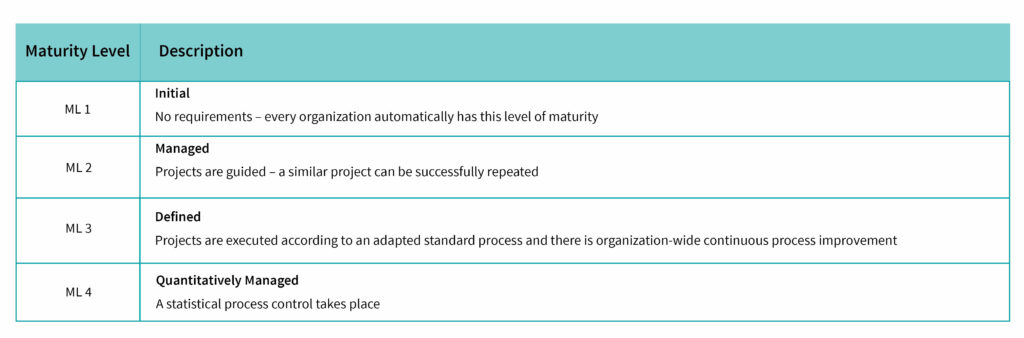
Technology with TÜV stamp means that the signs must already point in the direction of security when designing devices and subsystems. In the case of PLCnext Control, attention was paid to so-called “security-by-design” at an early stage of development and the secure development process according to IEC 62443-4-1 was applied. Part 4-1 of the “IT Security for Industrial Automation Systems” family of standards defines the secure development process – as basic work, so to speak. The focus is on identifying and closing potential security gaps as early as the conception phase. This is where we reach maturity level 3 (ML3), which stands for the repeatability and verifiability of processes throughout the organization. This is followed by the functional scope of a product. Our open control platform is the first in the automation industry with integrated security “ex-factory” according to the requirements of IEC 62443-4-2 for Security Level 2 (SL2). SL3 can also be achieved via the current SL2 status. For us, a SL4 level does not make sense, because we want a PLC with integrated security and not a security concept that can do a bit of PLC.
Overview of security levels and their meaning:
Overview of Maturity Levels and their meaning
Security over the entire life cycle
Certified, installed – ready to go? Unfortunately, cyber security at OT level is similar to classic virus protection in IT: upgrades determine daily activities. The classification into a security level forms an important basis – but only the basis. Recurring reports of damage and production downtime caused by hackers show that OT security must be considered over the entire lifecycle.
That’s why it makes sense to create a holistic security concept: Safe products, safe solutions, safe services. A 360-degree approach that Phoenix Contact has been pursuing for a long time. This triad is surrounded by professional vulnerability management. The Product Security Incident Response Team monitors security messages for the components used in the products and ensures the long-term availability of updates. Sophisticated complete solutions in combination with consulting and service are the measure of all things to make systems in production secure.
Long-term cyber security offers lasting protection. And this protection is more in demand than ever, especially in automation technology. “The threat situation has changed,” says Lutz Jänicke (Industrial Security Expert at Phoenix Contact). Initially, automation was out of sight, and protection was primarily directed at CRITIS facilities – critical infrastructures in nine industries: Energy, Water, Food, Government and Administration, Transportation and Traffic, Finance, and Insurance, IT and Telecommunications, Media and Culture, and Health. Today, hackers have long since stopped targeting critical infrastructure.
Customer benefits of this certification
– Classification into security levels and clearly described deployment scenarios (security context) form an important basis for a reliable and holistic security solution.
– Certified security level 2 with just one click, thanks to the pre-installed security profile.
– Advanced security features enable optimal interaction between IT and OT.
– The open automation platform is the first in the industry to meet the requirements of IEC 62443-4-1 Maturity Level 3 (ML3) and an IEC 62443-4-2 Security Level 2 (SL2).
This makes it easier for machine and plant manufacturers to design their solutions in such a way that they are better equipped to withstand hacker attacks.
– Easier implementation of automation solutions with security, thanks to pre-installed features such as: Firewall, VPN-encrypted communication,
authorization of users and software components, logging, backup and restore, and device and update management.
– Online, comprehensive security information center that explains security measures and use cases in detail.
– Quick identification of system relevant SL2 security features thanks to the IEC 62443-4-2 Component Requirement Compliance list.
– Factory pre-installed security systems can reduce the need for additional costly security systems and allow for a streamlined and simple overall system design.
– Good interaction with other Phoenix Contact products developed according to the 360-degree security concept
Conclusion
Nowadays, the security of OT systems can no longer be limited to the operation of critical infrastructures. With the revised Network and Information Systems Security Directive (NIS2), the European Commission therefore aims to raise cyber security to a higher level. In doing so, a significant expansion of the scope is defined for medium and large companies as well as other sectors important for the security of supply. In the future, cybersecurity will therefore no longer be an issue for larger companies alone but will also affect medium-sized businesses. A system that already meets security standards ex works and is certified makes implementation easy – and systems more secure.
You want to read more about industrial cyber security?
In case you want to read more about industrial cyber security we welcome you to Phoenix Contact´s main page about industrial security. Discover the full potenial of a 360-degree security contect and get inspired by the holistic product and service portfolio of Phoenix Contact: Industrial security | PHOENIX CONTACT
We also invite you to read our latest blog post about cloud security. Read in detail how a holistic cloud security concept not only saves time and money, but also protects against manipulation, data loss and unauthorized interventions: Cloud Security – A detailed Look – PLCnext Technology (plcnext-community.net)