NIS 2 unveiled: A game-changer in EU cybersecurity
Get ready to mark your calendars because a game-changer is on the horizon! Starting October 18, 2024, the EU’s groundbreaking cybersecurity directive, NIS 2, becomes the law of the land. This binding regulation sets the gold standard for cybersecurity across the European Union, compelling companies from diverse sectors to substantiate their cybersecurity efforts. We are ready for a strong cybersecurity with NIS 2!
As part of this year’s Cybersecurity Awareness Month, we’re on a mission to equip you with the vital insights into NIS 2. So, what exactly is NIS 2? Let’s dive in and explore!
What is NIS 2?
NIS 2 demystified: NIS 2 (Network and Information Security 2) represents the European Union’s response to the ever-evolving cybersecurity landscape. It’s the successor to the original NIS Directive, which came into force in 2016. The primary aim of NIS 2 is to bolster the cybersecurity defenses of EU member states and critical infrastructure by enforcing stricter regulations.
Legal mandate for cybersecurity: The directive transforms cybersecurity from an optional strategy to a legal requirement. Companies across various sectors must not only defend against cyberattacks but also prove their compliance with NIS 2’s rigorous cybersecurity measures.
EU member state obligations: EU member states have a pivotal role in NIS 2 implementation. They are tasked with submitting lists of essential companies that will undergo thorough cybersecurity evaluations every two years, ensuring a robust defense against evolving threats.
Cybersecurity risk management measures: NIS 2 defines a comprehensive framework for managing cybersecurity risks. It encompasses technical, operational, and organizational aspects. Key components include risk analysis, incident management, business continuity, supply chain security, secure development practices, and more.
Cyberattack reporting requirements: NIS 2 sets clear guidelines for reporting cyber incidents. Critical and important facilities must swiftly notify national Computer Security Incident Response Teams (CSIRTs) or relevant authorities. The reporting process consists of three stages: a preliminary report within 24 hours, a full report within 72 hours (including an initial assessment), and a final report within one month of the incident detailing its nature and cross-border impact.
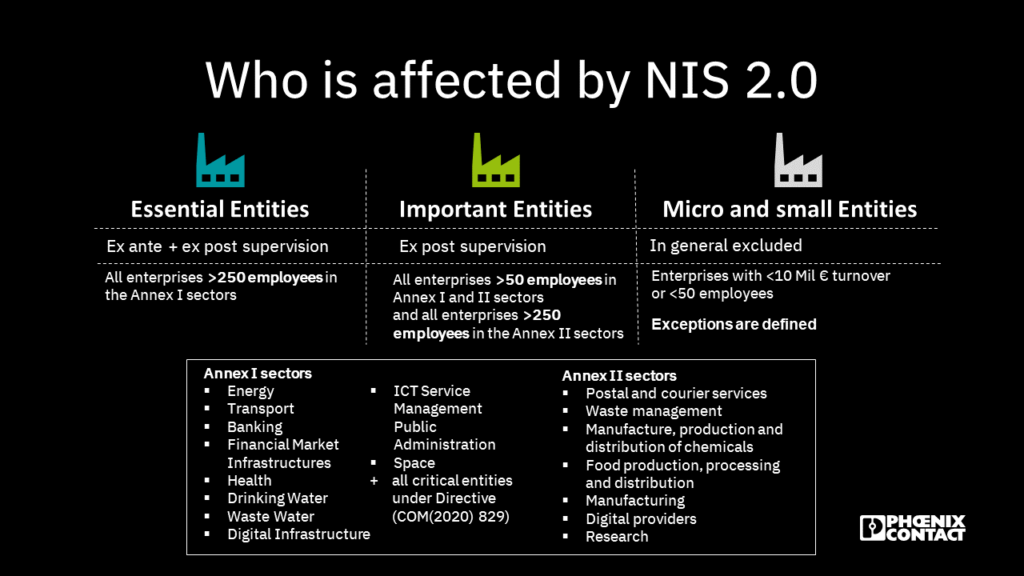
Who’s in the spotlight?
Tick-tock, the countdown to October 17, 2024, echoes loudly in the ears of every company operating within the European Union. It’s the day when all 27 EU member states must have seamlessly incorporated the formidable NIS 2 cybersecurity regulations into their national laws. But the pressing question remains: which companies find themselves under the scrutiny of the NIS 2 Directive’s unyielding gaze?
- Essential entities: First in the spotlight are the “essential entities”. These are the organizations entrusted with the lifelines of our modern world, operating within the realm of critical infrastructure. This includes, for example, energy, transportation, water management, healthcare, or banking. The NIS 2 umbrella unfurls over these vital sectors, compelling them to fortify their digital defenses.
- Important entities: But the reach of NIS 2 extends further. It also encompasses “important entities”. These are the gears that keep the machinery of our everyday lives turning. This category includes the stalwarts in food and chemical manufacturing, as well as those responsible for crafting the electrical equipment, machinery, and vehicles that drive progress.
And here’s an intriguing twist – member states themselves hold the power to broaden the NIS 2 net. They can include additional entities on their national lists, casting a cybersecurity umbrella over local authorities, educational institutions, and more.
Know the Stakes – Consequences for Non-Compliance
Here’s the stark reality: NIS 2 isn’t a mere formality. It’s backed by stringent enforcement, including heavy fines for non-compliance or failure to meet reporting obligations. The severity of these fines is contingent on your company’s categorization – “important” or “essential”.
For companies classified as “important“, the fines are substantial. They can range from seven million euros or up to a maximum of 1.4 percent of total annual global revenue in the previous fiscal year. These penalties underscore the importance of cybersecurity measures.
Now, consider “essential companies“, those entrusted with safeguarding the core of critical infrastructure. Non-compliance carries an even heftier price tag. They could face fines of up to ten million euros or a maximum of two percent of their total global annual turnover. The message is clear – cybersecurity diligence is not negotiable.
Crucially, it’s the top management’s duty to spearhead the implementation and monitoring of these cybersecurity measures.
Let’s get prepared together!
In the dynamic world of cybersecurity, change is a constant, and the introduction of the NIS 2 directive underscores this fact. While we await its adoption into national law for full effect, the urgency to take action is undeniable.
To meet the rigorous requirements of NIS 2, it’s crucial to build upon European and international standards as our cornerstone. These standards not only define secure products but also establish the principles for implementing resilient systems. One standout example is IEC 62443, a globally recognized series of standards for security in automation. Our holistic 360° security concept encompasses both technical and organizational measures, all backed by relevant IEC 62443 certifications.
A Secure Development Process: At the core of product development and throughout their lifecycle lies a secure development process, as delineated in IEC 62443-4-1. This process defines development using established cybersecurity practices such as Security-by-Design and Defense-in-Depth. It ensures continuous vulnerability monitoring and the timely application of security updates.
Certified Secure Products: In our pursuit of a 360° security concept, PLCnext Control takes center stage as the first controller in the market to achieve certification according to IEC 62443-4-1 ML3/4-2 SL2 Feature set by TÜV. This certification extended to many other products in the PLCnext Control family, guaranteeing Security-by-Design both during development and throughout the product’s lifecycle. The IEC 62443-4-2 Security Level 2 certification proves invaluable in meeting forthcoming EU regulations like NIS2, CRA, and MVO.
Secure Services: Our security specialists will advise you on how to minimize the individual security risks in your plant and, if you wish, will draw up a security concept – certified in accordance with IEC 62443-2-4. In addition, we pass on our knowledge in training courses to make your employees fit for cybersecurity.
Secure Solutions: For various solutions and markets, we’ve crafted templates (blueprints) that, when applicable, are certified in accordance with IEC 62443-3-3. These templates simplify discussions and conceptual work while showcasing Phoenix Contact’s ability to certify solutions in collaboration with customers.
Together, let’s embark on this journey towards fortified cybersecurity. NIS 2 serves as a call to action, and we stand ready to ensure your preparedness for the ever-evolving landscape of digital security.