Restricted mobile access: protecting a WLAN by password
Unauthorized smart devices must not be able to connect themselves via the WLAN interface. For that reason, your strict password rules should also apply to all wireless access points in your ICS.
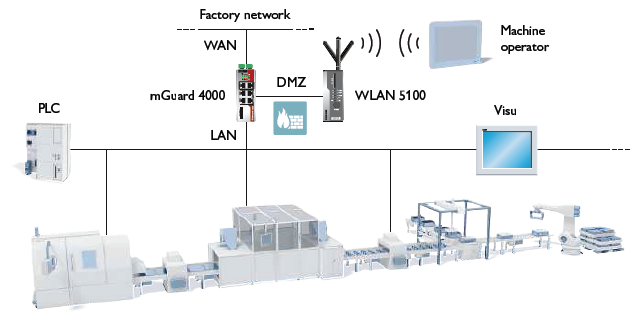
WLAN components from Phoenix Contact enable automated key management by the machine control system. This means that secure WLAN machine access can be easily implemented in the form of one-time passwords. In addition, WLAN communication can be protected and isolated from the rest of the network using a demilitarized zone (DMZ). The following figure shows an example of a secure integration of mobile end devices with one-time passwords and DMZ.
• Published/reviewed: 2025-02-10 • Revision 017 •