Remote access/remote maintenance
Consideration: risks and benefits
The increasing network capabilities of devices used to build automation infrastructures and systems enable a variety of new opportunities. Remote access to systems and data facilitates monitoring and maintenance of plants via the Internet. This saves costs, shortens the response time to problems that arise during operation, and can significantly reduce the risk of a production stoppage. Specialists no longer need to be on site to avert damage or loss.
However, where remote access is possible, misuse is also possible. Devices that are connected to a network via Ethernet are generally at risk of unauthorized network access. To prevent unauthorized third parties from accessing devices (controllers, switches, etc.) and making changes or corrupting/stealing data, appropriate access control measures must be taken.
Devices with communication interfaces (e.g., controllers) but without any built-in network security functions should never be used in security-critical applications without a suitable security appliance.
Note that unauthorized access can also occur, for example, via the following device interfaces: USB ports, PCI express interfaces, Ethernet interfaces, bus interfaces (e.g. Axioline or Profinet), SD card slots, device HMI (such as touch panels and other operating elements).
Making remote access controllable
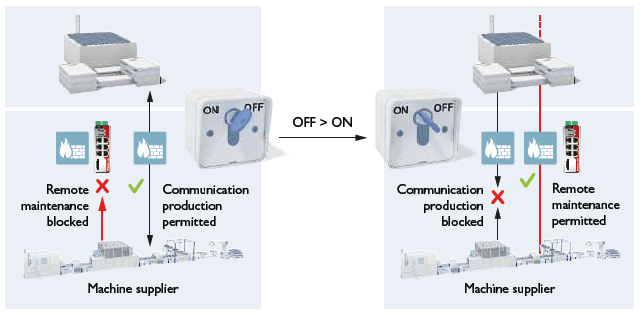
Basically, remote access should only be possible "on demand". For this purpose, the plant can be switched to a special maintenance mode, for example, by means of a key switch. In maintenance mode, the equipment may only operate with special attention to operational security and safety.
An implemented firewall should provide an appropriate configuration for this mode, e.g. by blocking (retroactive) effects to the production network. Furthermore, access must be restricted to actually required interfaces. If, for example, only access to the desktop transfer is enabled, the risk of malware infection is significantly reduced.
For your use case, check the possibility of disabling active communication channels (e.g. SNMP, FTP, BootP, DHCP, HTTP, HTTPS etc.) or assigning passwords.
Take further protective measures according to the IT security requirements and the applicable standards for your area of operation to prevent unauthorized access to your network. Such measures can be:
- Virtual networks (VPN) to ensure encrypted communication.
Note that the establishment of (encrypted) VPN connections directly to the remote maintainer must be viewed particularly critically, since there is no control over the actions performed via the VPN connection.
For securing networks for remote maintenance via VPN, Phoenix Contact offers the mGuard product line as a security appliance. Refer to the current Phoenix Contact product catalog (phoenixcontact.net/products).
- Use of secured communication channels. For example, data is transmitted encrypted using HTTPS (Hypertext Transfer Protocol Secure). Furthermore, the communication partners involved may have to authenticate themselves with certificates when establishing the connection.
- Installation of a key switch on the machine to initiate or inhibit remote access. The figure below shows an example.
A key switch ensures that only intended changes can be made to the machine. At the same time, the key switch also enables the communication rules in the network to be blocked while remote maintenance is being carried out. - Secure passwords for all access ways to ICS devices. This should also include access from mobile end devices via WLAN.