Generic security concept
Defense-in-depth design of automation systems is an important IEC 62443 process measure to achieve reliable security. The result is a generic layered architecture that leads step-by-step to a fully segmented network layer structure that describes the PLCnext Technology security architecture and the security use cases in the so-called security context.
The security context results from the combination of technological and organizational measures required by the IEC 62443 standard and the philosophy of a holistic security approach.
Defense-in-depth concept
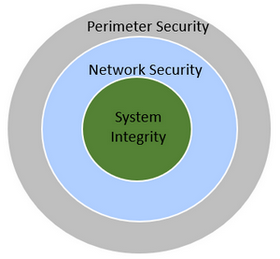
A generic defense in depth design results in three layers or zones:
- Perimeter security
Perimeters are the outer boundaries of the network,
protected by physical measures such as fences, doors, physical access controls, etc. - Network security
This layer contains the enterprise or office zone and a service management zone, protected by well-known IT security concepts. - System integrity
This layer contains OT devices and applications,
to be protected by IEC 62443 concepts.
PLCnext Technology security context
The following figure shows the PLCnext Technology generic security context (zones and conduits) focussing on the OT security based on IEC 62443-4-2 requirements.
- Blue-green connections (―) represent security mechanisms (e.g. TLS / HTTPS).
- Red connections (―)represent virtual private networks (VPNs).
.png)
The different layers (zones and conduits) are marked by numbers:
| No. | Description | Details |
| 1 | Data Repository Server | Provides data for patch management/asset management. |
| 2 | VPN Server | Remote maintenance access via VPN |
| 3 | Enterprise / Office zone | Factory IT; ERP (Enterprise Resource Planning) systems; production control systems. Protected by firewall |
| 4 | Service management zone | This zone can be considered as a Demilitarized Zone (DMZ) as it decouples the ICS networks (zones 5 to 7) from the external network by strictly controlling the information flow. Any communication between the external and ICS networks must pass this zone. Implements central user management, patch/update management, and logging. It contains the following infrastructure:
|
| 5 | System integrity | Factory OT, consisting of zones 6 to 8 |
| 6 | Manufacturing zone | Management, monitoring and controlling of the main process and the sub-process. Implements SCADA, time synchronization and engineering. This zone is composed as follows:
|
| 7 | Machine level Main process |
Collects and processes of data from the process and the sub-process. This zone is composed as follows:
|
| 8 | Production line level Sub-process |
Performs a specific automation function in a peripheral unit (remote station). This zone is composed as follows:
|
The PLCnext Technology security context is based on the Defense-in-Depth concept providing six security layers (zones/conduits):
Perimeter Security - the outer layer
Access protection for the enterprise network by the following measures:
- Physical isolation
- Digital isolation by network segmentation
- Logical access controls
- Use of specifically configured firewalls. The specified firewall must correspond to the identified threats and vulnerabilities.
- VPN or other security measures for remote access
- Documentation of all remote access points
Network Security layers
Protection of the factory network composed of the enterprise network zone and the service management zone which is considered as Demilitarized Zone (DMZ). Possible measures are:
- Identifying all network devices and hosts
- Analysis of protocols/traffic
- Auditing of wireless communication/traffic
- Analysis of switch/router configurations
Measures in the DMZ:
- OS check for vulnerabilities
- OS patch management
- USB or removable devices prevention from use inside control room
- Foreign computers restricted from connecting
System Integrity - the inner layers
Measures for SCADA applications:
- Monitored network for clear text transfer and use of encryption
- Ensured use of individual user accounts
- Restricted access to desktop
Measures for control subnetworks layer at machine/production line level (main process and subprocesses):
- Wired vs. wireless communications
- Ethernet vs. serial communications
- Capture traffic on Ethernet connections
Measures for field controllers:
- Ethernet vs. serial connected devices
- Ethernet devices tested in lab for vulnerabilities
- Removed vendor default passwords
Details on the possible measures can be found in the Security measures topic.
