OPC UA discovery/connection options
X509_V_FLAG_X509_STRICT. As firmware 2024.0 LTS is updated to OpenSSL 3.0, the X.509 certificate validation became more strict, especially for non self-signed certificates. This may cause the server to return the error BadSecurityChecksFailed on client connection attempts. Make sure that, according to OPC UA Part 6, client issuer as well as client application X.509 certificates are conform to RFC 5280, especially to the sections listed below. The same applies for user-managed server certificates.
- 4.1.1.2 signatureAlgorithm
- 4.1.2.6 Subject
- 4.2.1.1 Authority Key Identifier
- 4.2.1.2 Subject Key Identifier
- 4.2.1.3 Key Usage
- 4.2.1.6 Subject Alternative Name
- 4.2.1.9 Basic Constraints
Server
The eUA server provides an ApplicationDescription with the fields ApplicationUri, ApplicationName and DiscoveryUrl. These fields include the HostName, which is either the IP address of the controller or the DNS name (DNS Name / IP Address input field in PLCnext Engineer).
Endpoints
The eUA server offers an endpoint to which the clients can connect. In its URL, you can either configure the IP address of the controller or the DNS name. Implement the configuration in the PLCnext Engineer software:
- In PLCnext Engineer, open the OPC UA node in the PLANT area.
- In the Basic settings, enter either the DNS name or the IP address in the input field.
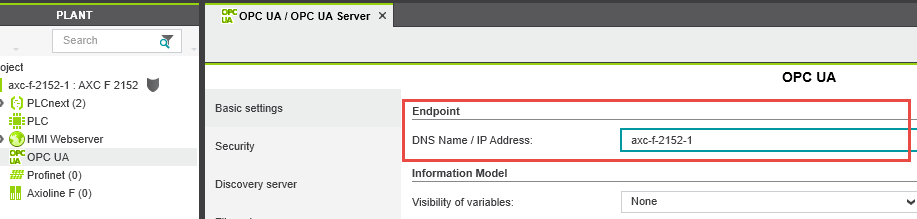
More information on configuring the host name can be found in the PLCnext Engineer Online Help. It can be found within the software under Help → View Help menu, or online (from software release 2022.0 LTS).
Ethernet ports at the controller
Up to and including firmware version 2022.6, there is no mapping to a certain Ethernet adapter at the controller. Therefore, a connection is possible via all adapters.
As of firmware version 2022.9, this only applies when using a DNS name in the Endpoint input field (DNS Name / IP Address).
If an IP address is used, the OPC UA server can only be contacted via the Ethernet adapter this IP address is assigned to (it cannot be contacted via the other Ethernet adapters of this controller).
In many factory automation networks there is no DNS server used to resolve the DNS name of the controller into its IP address. Therefore, it is recommended to enter an IP address in the input field for the Endpoint.
Encryption algorithms
The eUA server provides endpoint description for each security configuration.
Supported Endpoint Configuration:
| Security Policy | Message Security Mode | User Identity Token |
| None** | None** | Anonymous** |
| Basic128RSA15* | Sign | Username/Password, Anonymous |
| Basic128RSA15* | Sign and Encrypt | Username/Password, Anonymous |
| Basic256* | Sign | Username/Password, Anonymous |
| Basic256* | Sign and Encrypt | Username/Password, Anonymous |
| Basic256Sha256 | Sign | Username/Password, Anonymous** |
| Basic256Sha256 | Sign and Encrypt | Username/Password, Anonymous** |
| Aes128Sha256RsaOae | Sign | Username/Password, Anonymous** |
| Aes128Sha256RsaOaep | Sign and Encrypt | Username/Password, Anonymous** |
| Aes256Sha256RsaPss | Sign | Username/Password, Anonymous** |
| Aes256Sha256RsaPss | Sign and Encrypt | Username/Password, Anonymous** |
*Note: By default, the Basic 128 RSA15 encryption algorithm is not activated as this algorithm is no longer regarded as secure. However, you can activate this algorithm to be able to connect the eUA server to older OPC UA clients that at most support this algorithm.
**Note: Not regarded as secure. Therefore it is disabled and not recommended but available if the PLCnext Technology user authentication is disabled.
Server Certificate
The eUAServer identity ServerCertificate is held by the PLCnext Technology certificate store infrastructure.
The OPC UA identity store is configured depending on the server certificate configuration:
| Server Certificate | Identity Store |
| Self signed by controller | OPC UA-self-signed |
| File on controller | OPC UA-configurable |
| Provided by OPC UA GDS | <ServerIdentityStore> |
Note the following for the server certificates:
- Self signed by controller:
The controller stores a certificate in the Identity Store OPC UA-self-signed. This certificate is newly created during the project download if the OPC UA® security settings in PLCnext Engineer have been changed. In case the identity store is empty the eUA server will generate a key pair and create a self-signed certificate if the self-signed option is selected.
OPC UA-configurable is used as the Trust Store. Via WBM you can store the certificates for the trusted clients. As long as the trust store is empty, the firmware accepts every client. - File on controller:
In this case the Identity Store OPC UA-configurable is used. Via WBM you have to store certificate and private key.
OPC UA-configurable is used as the trust store. Via WBM you can store the certificates for the trusted clients. As long as the trust store is empty, the firmware accepts every client. - Provided by OPC UA GDS:
You can specify a name for an Identity Store and a Trust Store. The certificates distributed by the OPC UA GDS Server are stored there. You can find an overview of the stored certificates in the WBM. Do not make any changes in the WBM, because these two stores are managed via OPC UA GDS.
Note:
- The following applies to all configurations: "Reset to default setting" deletes all Identity and TrustStore settings.
- Many OPC UA® clients check if the server certificate contains the used IP address or DNS name. Therefore, these have to be contained in the server certificate as subject or alternate subject. This rule hold true regardless whether Self signed by controller or a different option is configured. In case of Self signed by controller the controller uses the values entered in the input field Endpoint (DNS Name / IP Address) as subject for the self signed certificate (so if DNS name is used it may be necessary to additionally configure the IP address as subject in the section Security of the OPC UA® server editor in the PLCnext Engineer project) .
To configure the server certificate configuration, refer to Server certificate.
To manage certificates, refer to Certificate authentication.
Security Policy
The eUA server supports the following security policies for message signing and encryption:
- Basic 128 RSA15
- Basic 256
- Basic 256 SHA256
- Aes128Sha256RsaOaep
- Aes256Sha256RsaPss
By default, the Basic128Rsa15 and Basic256 encryption algorithms are disabled as these algorithms are no longer regarded as secure. However, they can be activated for older OPC UA clients that at most support these algorithms, through eUA server configuration.
To configure the security policies, refer to Security policies.
Security Mode
The eUA server enables message security mode Sign as well as Sign and Encrypt for encrypted endpoints by default.
SecurityPolicy#NONE is disabled by default but is enabled if PLCnext Technology user authentication is disabled (not recommended).
To disable user authentication refer to User Authentication.
Note: If the user authentication is disabled, the OPC UA® client does not have to authenticate itself to the OPC UA® server. This way, unrestricted access to the OPC UA® server and the PLCnext Control device is possible.
User Identity Token
The eUA server supports username identity tokens with password for encrypted endpoints by default. Username identity tokens are not supported for non-encrypted endpoints.
The anonymous identity token is disabled by default. To enable the anonymous identity token, user authentication shall be disabled.
To disable user authentication refer to User Authentication.