Security and safety hardening
To use PLCnext Technology as an IEC 62443-4-1/4-2 certified component, the activation of the Security Profile is mandatory. In addition, the automation system design must fit the security context and the generic use cases described in this PLCnext Technology ‑ Security Info Center.
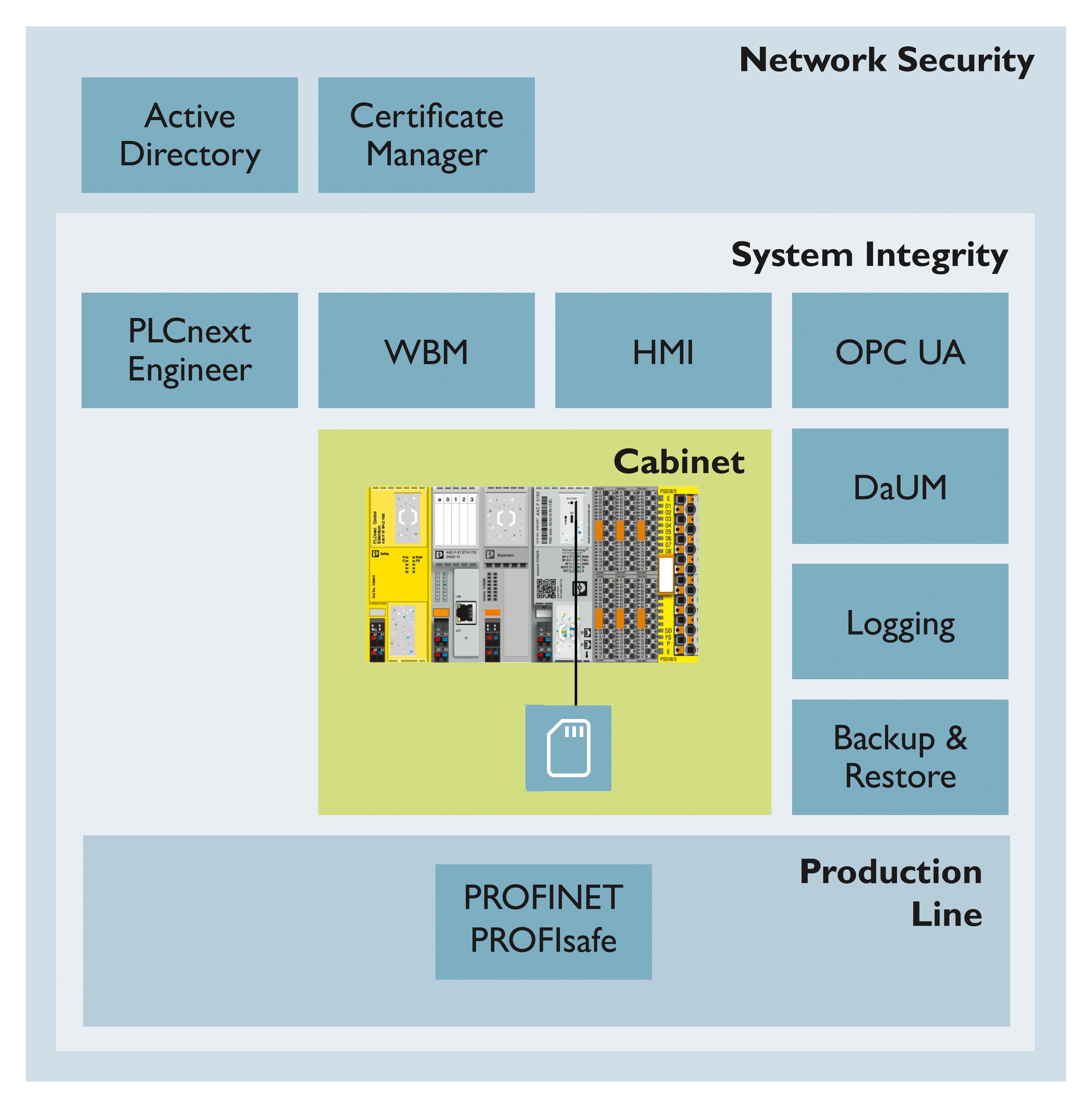
With activated Security Profile PLCnext Technology supports the following functions as shown in the topic PLCnext Technology security hardening .
Additional security measures for functional safety:
- Additional user roles (SafetyEngineer and SafetyFirmwareUpdater)
- Protected file system area by special access rights
- PROFINET / PROFIsafe®
Measures for functional safety:
- Left-alignable safety-oriented control SPLC 1000
- Dual password protection:
- Safety PLC Password to access the safety controller
- Project password to enable safety-related editing of the project
- Safety logs are accessable via PLCnext Engineer, see the online help of PLCnext Engineer.
- In PLCnext Engineer, the safety-related and the standard application are separated, see the online help of PLCnext Engineer.
- Combined or distinguished download of standard project and safety-related project
For further information, refer to the topic Configuring PLCnext Engineer (combined safety).
Security and safety architecture
To fulfill the IEC 62443-4-1 requirements a threat analysis of the PLCnext Runtime System and PLCnext Technology hardware is an important task. The PLCnext Technology threat analysis is based on the STRIDE model which consists of the identification of these security threats in these categories: spoofing, tampering, repudiation, Information disclosure, denial of service, elevation of privilege.
As a prerequisite the security context defined in this PLCnext Technology ‑ Security Info Center and the implemented Security Level 2 (SL2) feature set are used.
One key element of the threat analysis is to review the integrity and authenticity of the data in rest and data in transmission. Another key element is the authorization of human users and software components to access the data. In addition, the firewall protects the access to the communication interfaces, or supports denial of service protection.
PLCnext Technology provides TLS 1.2 or TLS 1.3 based communication on necessary communication interfaces (e.g. HTTPS, OPC UA®, PLCnext Engineer).
For other communication channels like LDAP or Syslog-ng, TLS can be activated according the users’ needs.
The authorization is handled by an RBAC user management for human users, and/or certificate management for software components.
Functional safety with PROFINET / PROFIsafe® communication
PLCnext can be enhanced by a powerful two-channel safety-related controller for PROFIsafe®. Either as left assignable modular hardware module or an additional functional safety hardware module designed in the housing of the controller by default.
Secure and safe communication is handled via PROFINET and PROFIsafe® technology. The PROFIsafe® functional safety protocol is transmitted via the PLCnext Control device using the PROFINET network by the black channel principle.
Before setting up a PROFINET network a risk analysis must be done and an sufficient security context must be designed. Please refer to your PLCnext Control description (e. g. AXC F 2152 ) and the controller manual to setup a secured and segmented PROFINET network.
The functional safety controller (SPLC) is protected by a defense-in-depth layer approach. The IEC 62443-4-2 certified PLCnext Control protects the SPLC against security attacks (see Certified secure development lifecycle ). An SPLCProxy layer is providing security extensions, dedicated safety roles and file system access rights to protect the SPLC. The SPLC has no direct connection to the network nor is storing data in rest on an own mass storage. It’s executing the functional safety logic downloaded by the PLCnext Engineer as well as using PROFIsafe® to manage the safety I/Os. SPLC is certified by IEC 61508 SIL3 (see Functional Safety Certificate) The security measures enhance the black channel security but don’t interfere the functional safety.

Security and safety measures
Data in rest
PLCnext Technology’s data is stored on an internal (non-removable) SD card. The detailed description of the data and directory structure can be found in the main PLCnext Technology ‑ Info Center at the Directories of the firmware components.
The SPLC only uses data of the SD card of the standard PLC, which is protected via the SPLCProxy, for data storage.
The controller can be expanded via an external SD card. An external SD card enables an easy device replacement with licenses transferred via that storage medium. You also get additional space for your automation project data. From firmware version 2022.0 LTS special SD cards are available supporting the distribution of licenses:
- SD FLASH 8GB PLCNEXT MEMORY LIC (item no. 1151112)
- SD FLASH 32GB PLCNEXT MEMORY LIC (item no. 1151111)
- SD FLASH PLCNEXT MEMORY LIC CFG (item no. 1308064)
From 2024.0 LTS, these special SD cards provide data protection, and therefore can be used together with the Security Profile.
Some controllers require an SD card for operation. Check in the topic of the respective controller whether your controller requires an SD card.
Phoenix Contact recommends to secure the slot for SD card on the PLCnext Control with a lead seal against manipulation. For further information about protecting the SD card, refer to the topics Protection against physical access and Secure disposal and the topic of the respective controller (e.g. AXC F 2152 ).
Data in transmission
To support secure communication e.g. via TLS, different options of cryptographic keys can be configured. For further information, refer to the topic PLCnext Technology security hardening .
User Management
PLCnext Technology’s User Management provides authentication and authorization on each communication interface. Only authorized users can access (read/write) data via a communication interface.
In the context of functional safety, PLCnext offers additional user roles. See the topic Creating users (combined safety) for more information.
Software information integrity and authenticity
Software information security is provided by different mechanisms. For further information, refer to the topic PLCnext Technology security hardening .
For information about the dedicated measures for functional safety, refer to the hardware documentation of your safety controller (Product range).
Mobile and malicious code protection
Authentication and authorization are provided by the User Management: Only authorized users get access (read/write) to the SPLC's data.
PLCnext Engineer enforces the user to enter his credentials before accessing the controller. Only authorized users can download an application to the SPLC device.
See the topic Creating users (combined safety) for more information.
Safety projects are checked via CRC before download, see the topic Security logging (combined safety).
Standard projects are checked via hashes, see the topic Checking project data integrity.
See also the topic Configuring PLCnext Engineer (combined safety) for measures of functional safety.
Access protection
Protection against physical access
- Install the PLCnext Control in a lockable housing or a lockable control cabinet.
- Consider the information from the topic Protection against physical access.
Protection against unauthorized data access
To protect against unauthorized data access, a log in is required e. g. via PLCnext Engineer.
Every user has specific user roles managed via the user management. To have access to the data, the user must have access rights to standard and functional safety data. Therefor, the user "Engineer" can be configured to have two user roles (Engineer for standard data and SafetyEngineer for functional safety data), see the topic Creating users (combined safety).
In PLCnext Engineer, every user has to log in to have access to the PLCnext Control.

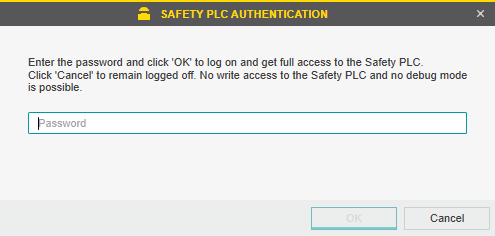
As an additional measure for functional safety, dual password protection is offered.
The safety PLC is protected by a controller password. Writing data to the safety PLC, switching its operation mode or executing debug commands is only possible after entering the controller password in PLCnext Engineer.
The safety-related project data are protected by a project password. Safety-related parts of the project can only be edited while being logged in.
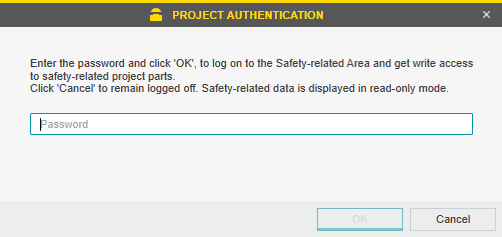
For further information about dual password protection, refer to the online help of PLCnext Engineer.
Safety logs in PLCnext Engineer
Any editing operations and messages in PLCnext Engineer that relate to safety-related project parts are written to the persistent safety message log, or safety log in short.

The safety PLC log messages editor page lists the entries which have been read from the log book of the safety PLC. In the log book, the safety PLC records device-related events such as state changes and errors.
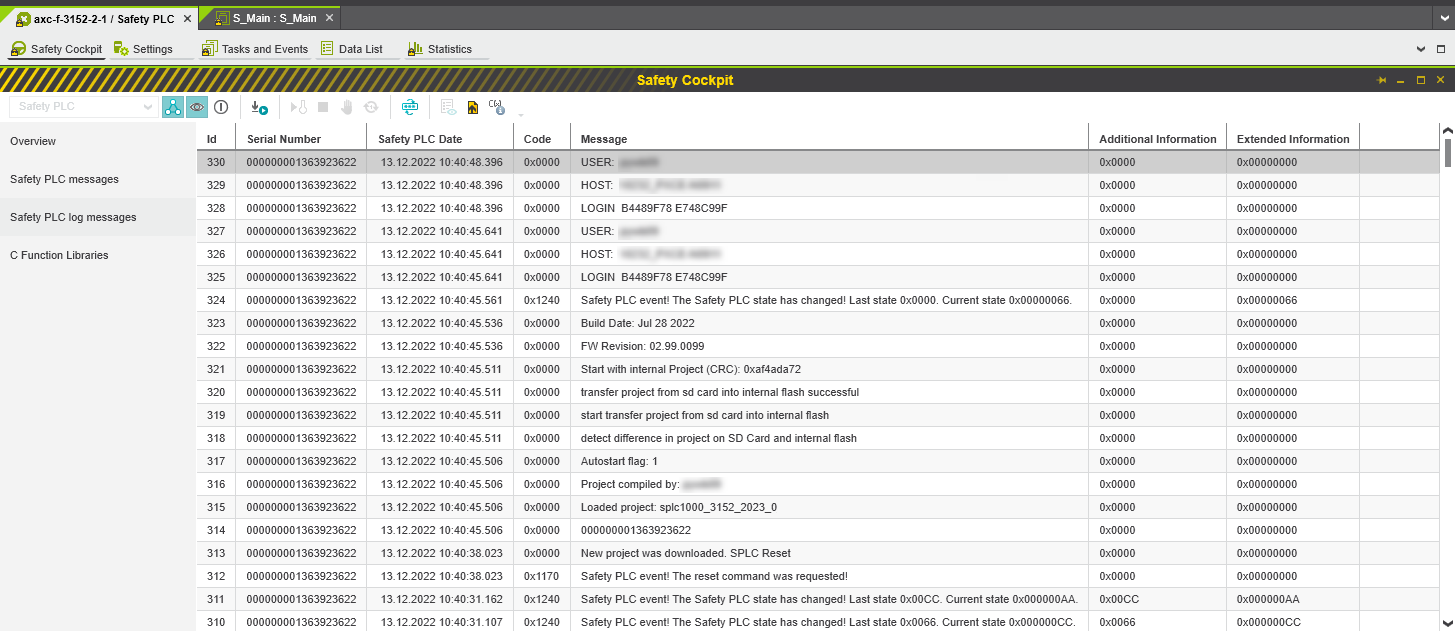
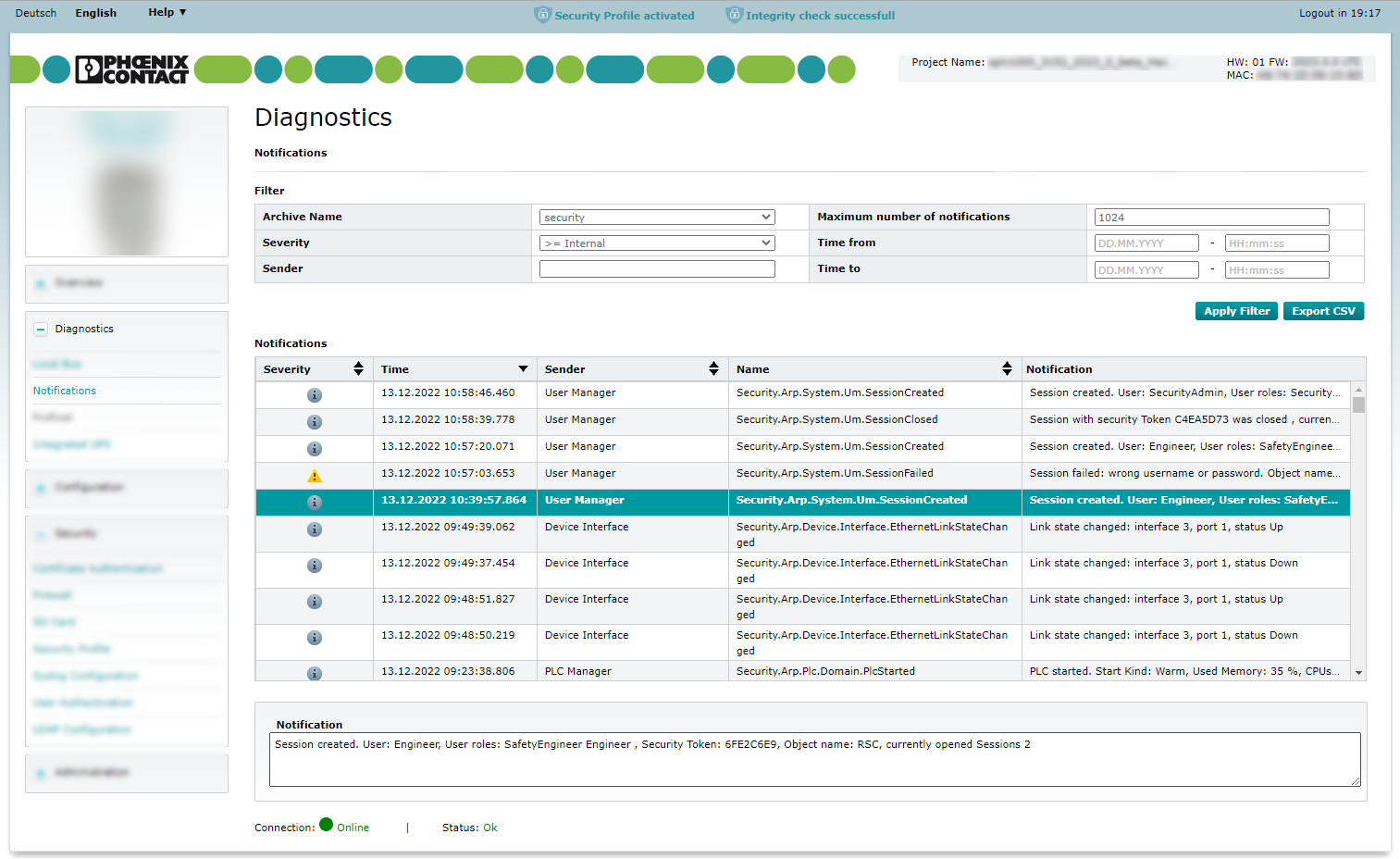
Security logging PLCnext
The SecurityAuditor has access to the notifications on the Notifications page (Diagnostics → Notifications) in the WBM. He can view all activities of the logged-in users and their user roles.
Combined or separated download of standard project and safety-related project
In PLCnext Engineer, you can download the standard project and the safety-related project combined or separated.
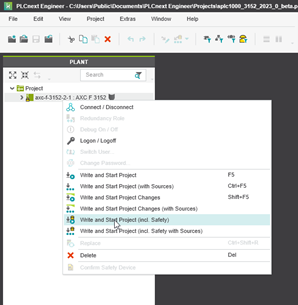
In order to perform a combined download, you have to configure the write and start commands first (see the topic Configuring PLCnext Engineer (combined safety)).